The Importance of Digital Transformation Seen through the Rediscovery of Data Utilization
Elice
5/18/2021
Byeong-hyun Ban recently published a book titled “Coding for the Common Good.” The book carries a somewhat provocative subtitle, “Can We Change the World Even While Wearing Shackles?” Ban majored in artificial intelligence at KAIST (Korea Advanced Institute of Science and Technology) for both undergraduate and graduate studies. He worked as a social service worker at the Andong Regional Labor Office before recently completing his military service. You might be wondering who he is at this point. In fact, Ban is more famous as a public servant who, rather than his career, became renowned for finishing a six-month task in just 30 minutes using coding and data utilization.
 Public service worker engaging in coding
Public service worker engaging in coding
Ban utilizing coding to handle tasks during his time as a public service worker garnered significant attention when it was shared on the blog site Brunch./Photo from book
Due to the sensational title claiming to finish six months’ worth of work in just 30 minutes, many people don’t know what he actually did during his social service. In one line, his task involved checking around 3,900 registration numbers on the post office website and printing out the details displayed on the screen. Afterward, Ban engaged in support activities for government agencies and administrative sites and received a commendation from the Minister of the Ministry of Administration and Safety in the government innovation sector in 2019.
Listening to Ban’s story, you might be impressed and think, “Wow, that’s amazing.” However, some might not understand, wondering, “Why would someone go to such lengths?”
The thought “Why go to such lengths?” is widespread. It’s precisely this thought that continues to consume people’s precious time and organizational productivity with repetitive tasks. Ban’s alma mater, KAIST, was no exception to this phenomenon.
From “manual grading” to “mechanical grading” through utilization of data
KAIST’s fundamental programming education has a long-standing tradition. Thanks to this, a significant number of KAIST graduates include not only early 2000s entrepreneurs who led many IT companies but also recent startup founders. Since 2015, every semester, around 400 students, totaling 800 freshmen per year, have been required to take the CS101 introductory programming course using the Elice platform.
One key feature of the Elice platform is its automatic grading system. For practical exercises done in class, students receive immediate feedback and scores simply by clicking the submit button. Students can modify their code and resubmit it to aim for higher scores. The platform also offers exams with set time limits and deadlines.

Professor Tae-sook Han of the Department of Computer Science at KAIST “What’s Important, Programming Lectures at KAIST”/KAIST
KAIST’s tradition of foundational programming education spans 50 years. However, before the development of Elice, around 30 teaching assistants manually graded the code of 800 students. Students would upload their code files to a forum, and teaching assistants would download and run each one individually for evaluation. Grading 800 pieces of code one by one sometimes led to grading sessions that stretched past 3 a.m. to meet the deadline. The very reason people learn computer science is to let machines do human tasks, yet those teaching and learning it often stuck to traditional methods.
The inefficiencies caused by this process served as a powerful motivation for former KAIST programming teaching assistants to develop the Elice platform. With the introduction of Elice, the mechanical grading tasks that were previously handled by human manual grading were transferred to the realm of machines. This shift allowed teaching assistants to provide better feedback to more students during the time that would have otherwise been spent on repetitive tasks.
News About Elice Solution’s Plagiarism Check Function
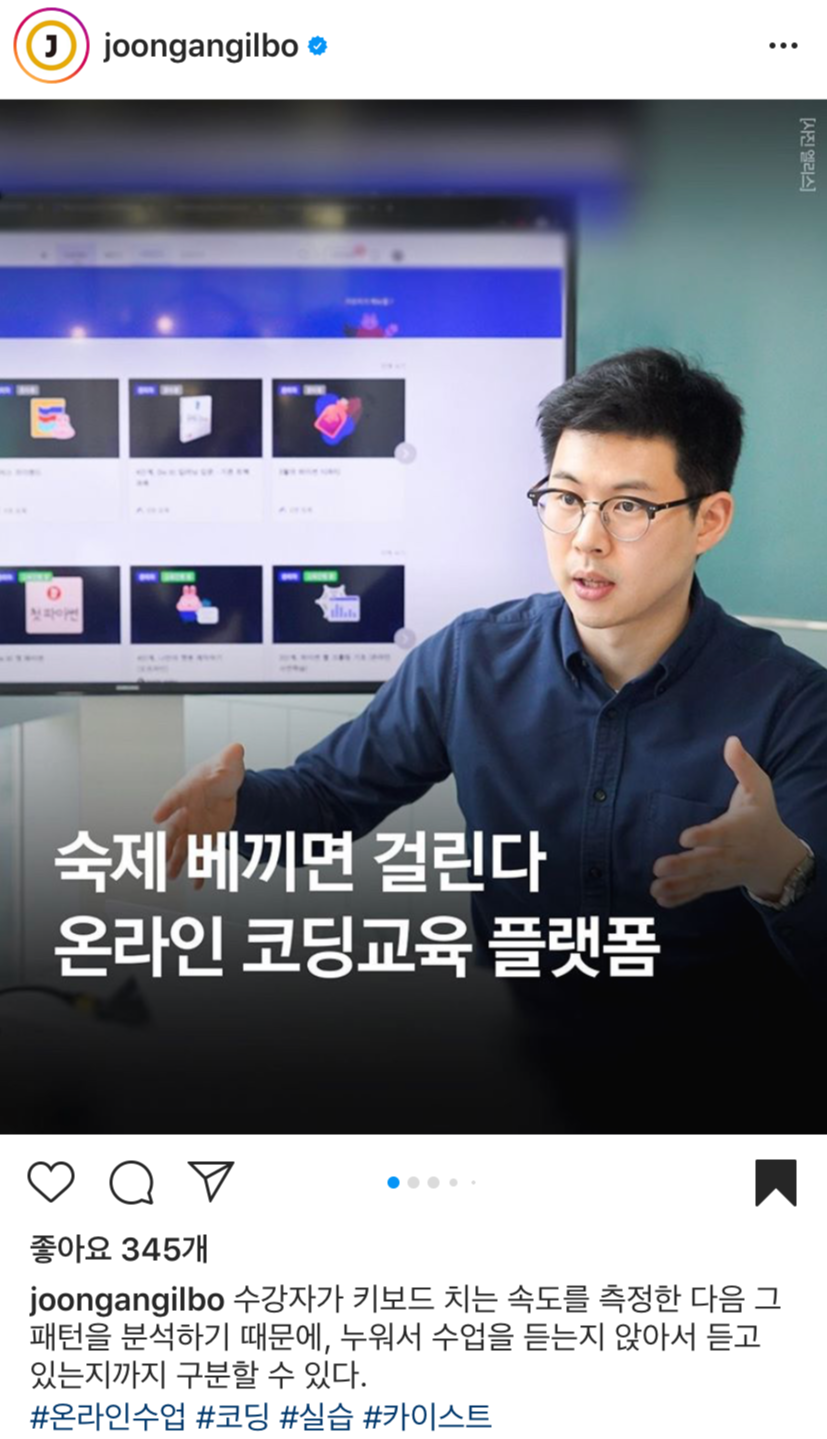
Not long ago, news about Elice was published on the Instagram of a media company.
Many commenters responded furiously to the message, “They can know whether you wrote the code lying down, sat up, just turned on the computer, or if you did it yourself.”
Although not the main feature highlighted in the news, what angered students was the “Copy Detector,” an anti-plagiarism system in the Elice platform. The reason such precise measurements are possible is that the code written by students in the Elice code editor is recorded at a granularity of one character. When there are suspicions of plagiarism in the submitted code, teaching assistants use the Copy Detector to display the distribution of similar code written by different individuals. They also meticulously examine the students’ writing history, documented character by character, much like reviewing a video, to determine whether the student completed the assignment based on their skills or mechanically copied someone else’s code.
The Copy Detector provides hints on which codes should be prioritized for review when there is a large number of codes to assess due to a high number of learners. The recorded data of code history are used to reconstruct patterns of learning behaviors necessary for the final judgment, presenting them visually. This prioritization aspect, indicating whom to review first during educational support or evaluation, is commonly utilized in practical university courses.
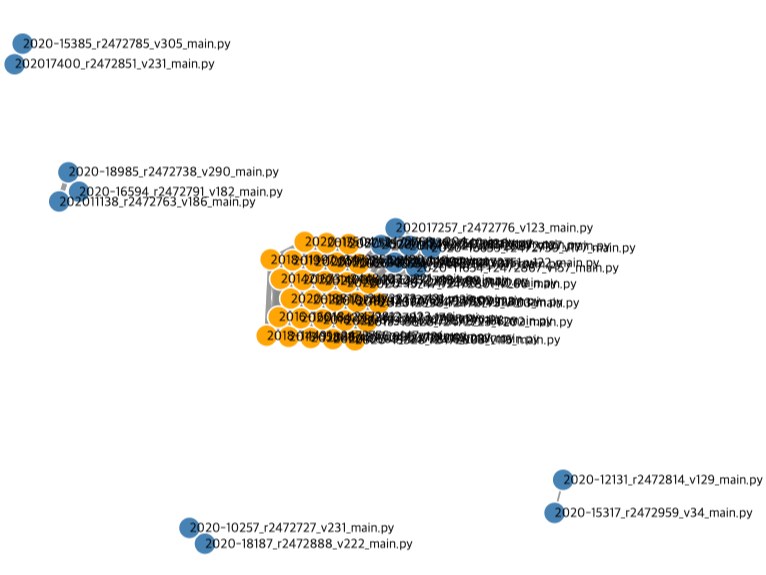
The copy detector execution screen is built into the Elice platform. Each point is a program written by a learner, with similar points being connected by lines.
When examining the code history of most learners, a pattern emerges: they write, delete, run the code, fix errors, and repeat these steps multiple times before submitting the final result. This pattern, although ordinary, represents the learning behavior of individuals with the highest growth potential. Those who deviate significantly from this pattern might either be naturally talented or raise suspicions of plagiarism.
The Democratic Party’s Big Data Use Case: The Perception That “Data Exists”.
Recently, in the conservative realm, the phrase “Why go to such lengths?” was frequently heard, even in the context of the elections. The three primary factors that typically influence elections are considered to be strategy, personalities, and funding. However, now there might be a fourth factor to consider: data.
The Democratic Party of Korea, which achieved a significant victory in the 21st general election, was reported to have utilized data in their election campaign, specifically the anonymized mobile phone usage information provided by telecommunications companies. Candidates, in particular, used data on areas and times where people gathered the most within their constituencies to plan their campaign routes, aiming to meet as many voters as possible.

Local constituency elections are crucial as they gather the votes of people candidates meet, making grassroots campaigning essential. Scenes from the final legislative council election campaign held just before the handover of Hong Kong./Alix Le
The crucial point here is the recognition that there is “data” available to achieve one’s goals. Being aware of this fact can alter the way situations are assessed, leading to different actions. Ultimately, these actions can result in different outcomes.
The Democratic Party’s election strategy was precisely based on this awareness that data exists, and it was meticulously planned with this in mind. The useful information provided contributed to the candidates’ victories. The utilization of data, specifically voter movement information within constituencies, is likely to become a standard in future elections.
Data Transaction Legalization and Data Utilization
Of course, this could be questioned differently: Didn’t we know these methods before? The news about the Democratic Party’s use of big data for candidate campaigning emerged just before the election. Frankly, this is not news; it’s more of an advertisement, a way for the party to showcase how smart they are through the media.
There have been candidates or parties in previous elections who attempted similar strategies. The difference lies in the passage of the so-called Data 3 Laws earlier this year, which allowed legal data transactions between political parties and businesses in this election.
The so-called “Data 3 Laws” passage expanded the types of data and scope of utilization that became legally tradable. /Policy Wiki
On the other hand, did other parties not utilize data in this election? There are two possible circumstances. First, they might have used it to maintain strategic advantage (but chose not to reveal it due to their defeat), or they simply couldn’t utilize it due to the substantial resources in terms of manpower and funds required. Although data trading has been legalized, significant amounts of expensive data worth millions, if not billions, along with specialized professionals to process and analyze it, require considerable time and resources to impact an election.
In the past, campaign strategies were often based on incomplete information (e.g., a new apartment complex appearing somewhere in the constituency recently) and judgments based on experience (e.g., seniors tend to visit in larger numbers at 7 AM on market days). There might have been Democratic Party candidates who did not utilize data for planning their campaign routes.
The Democratic Party, which already had overwhelming advantages in constituencies and resources, added extra detail through data utilization. In local elections where one vote can determine the outcome, every vote counts. Despite being the most conservative electoral arena, if there is data to borrow, there’s no reason not to. At this point, instead of saying “Why go to such lengths?,” one might find themselves saying, “Even to that extent?”
Amazon’s digital transformation didn’t happen overnight
The difference might seem subtle, but there’s a significant distance between these two expressions. It requires a shift in perception. If we dissect the term “digital conversion,” it means transforming the mindset for problem-solving into a format expressible through numbers.
Individual efforts or efforts of specific teams might not be enough, especially when this mindset shift needs to happen at an organizational level. What if someone is using digital tools but their approach to problem-solving still relies on past experiences, essentially heuristic reasoning? It’s akin to planting soybeans and waiting for red beans to grow.
In this context, the case of Amazon’s Editorial Team mentioned in the first paragraph, provides an interesting perspective. Today, Amazon is a colossal, complex, and expensive company that’s hard to define with a single adjective. However, Amazon also had ideas that were far from innovative in its early days. In its initial years, all Amazon employees would halt their work and join the logistics department during Christmas. Similarly, when Kakao Bank first opened its doors, around 250 employees were engaged in verifying the identities of the subscribers who were flooding in.

Amazon founder Bezos, within the prominent IT company Amazon, has instructed to write reports as concise documents of about one page with complete sentences, from the early days of the company to the present. /flickr
Among companies labeled as digital or IT enterprises, many were initially just logistics, distribution, or manufacturing firms. The key difference is that these companies didn’t simply stick with heuristic approaches. They adapted and constantly improved their methods of utilizing data to achieve digital transformation. Amazon, for instance, disrupted the massive industry sectors of distribution and sales by consistently refining their methods, and this transformation didn’t happen overnight.
What drives the successful transformation and improvement of digital enterprises? In the following text, we will explore what is needed for organizational-level digital transformation.
Read more:
👉Cases of DX training concerns and solutions for corporate education managers
*This content is a copyrighted work protected by copyright law and is copyrighted by Elice.
*The content is prohibited from secondary processing and commercial use without prior consent.
- #insight
- #tech
